Message-based connections enable system-level debug and validation

A key element in silicon lifecycle management is getting the right kind of data from your chip at key points in the silicon lifecycle, such as debug and validation. One of the “superpowers” of Tessent Embedded Analytics is its ability to securely capture functional data, via sophisticated monitoring IPs like our Bus Monitor and Static Instrumentation. (You can see all the Embedded Analytics products here). The nature of Embedded Analytics monitors sets them apart from structural monitoring technology like traditional DFT, and from very basic in-chip process, voltage and temperature (PVT) monitors.
These functional monitors help us understand the complete hardware-software system within the chip. But they are only part of the story. What’s just as important is the on-chip communications infrastructure that links the monitors into a co-ordinated whole. This is what we call the Secure Message Infrastructure or SMI.
What is the Secure Message Infrastructure?
The SMI is a secure, scalable communications fabric that functions independently from the chip’s main interconnect. It carries data from the on-chip monitors and makes that data available (via gateway IPs called communicators) to the outside world. It allows the on-chip monitors (and their internal counters and filters) to be configured at run time, either via a host or programmatically. This is a key capability in ensuring that the system can “measure what matters”. Just as importantly, the SMI allows the various Embedded Analytics IPs to send messages between themselves.
It’s tempting to think of the SMI as “just plumbing,” but it’s actually much more than that. For example, allowing the monitor IPs to intercommunicate is key to enabling what we call “any-to-any cross-triggering” – meaning that if a monitor detects a pre-defined behavior somewhere on the chip, it can trigger a monitoring action anywhere else within the Embedded Analytics infrastructure. So, if an NoC Monitor captures an event on the main system NoC, it can then initiate capture of processor trace from a CPU elsewhere on the chip.
Why SMI beats point-to-point interconnects
This is an important capability if your aim is to understand the behavior of the entire system. It’s also difficult to achieve using the point-to-point style interconnects used by traditional on-chip debug and validation systems. Why? Because using a point-to-point system requires the designer to know in advance which modules are going to need to communicate with each other: the monitors need to be “wired up” at design time. In contrast, a message-based architecture allows designers to take a more natural “bottom up” approach. The SoC can be designed hierarchically – with each subsystem including associated block-level monitoring subsystems. The blocks are brought together as the design progresses. An infrastructure like the SMI allows entire blocks to be duplicated and instantiated unchanged. Verification can also proceed hierarchically.
Also, point-to-point monitoring architectures are notoriously difficult to close for timing. In contrast, the SMI is non-blocking and includes retiming capabilities, meaning that data is never lost on the interconnect, but all events can be tracked in real time.
Advanced security features
As the name suggests, the SMI also includes advanced security features that allow all or part of the Embedded Analytics infrastructure to be locked down. The most obvious scenario when this is required is to prevent customers, end users or malicious actors from capturing information from inside the chip after deployment. But there are more subtle use cases, such as when a chip maker wants to selectively grant access to certain categories of information to a development partner. The SMI is equipped with a simple yet effective set of locks, distributed through the communications fabric, which allows for a broad range of these scenarios.
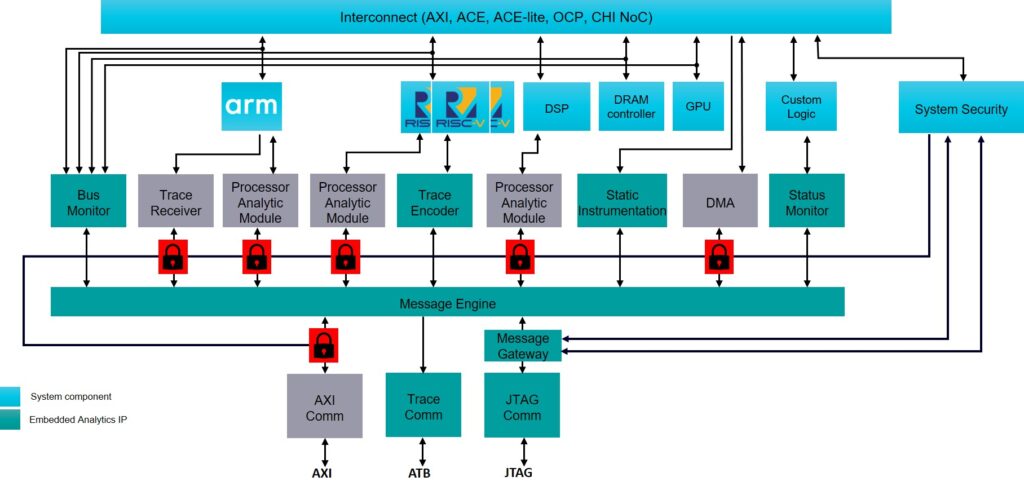
So, as you can see, the SMI is far from “just plumbing”— it’s the infrastructure on which Embedded Analytics relies to do the most effective job possible in helping to understand the behavior of an SoC. It provides a mechanism to protect the Embedded Analytics system from unauthorized access using a more flexible and robust architecture than what is currently available in point-to-point interconnects.
You can find out more about the SMI by downloading the product factsheet.