Introducing Polarion’s support for ISO 21434 and UN R155

End of June 2020, the UN released two new regulations, which were long awaited and are expected to not only protect vehicles against cyber-attacks but also protect passenger’s privacy. But let’s start at the beginning: The UN, precisely UN ECE with its working party 29 (WP29), provides regulations for safety aspects of vehicles since the 1950’s: safety belt, headlamp system or more recently emergency braking system to mention a few. With the digitalization of in-car-systems, raise of connectivity and shared mobility the number of electronic control units and amount of software code dramatically increases. A GSA and McKinsey report, published in spring 2020, estimates that cars currently have approximately 150 ECU with 100 million lines of code. It is expected to increase to 300 million by 2030. See the table below for some comparison figures.
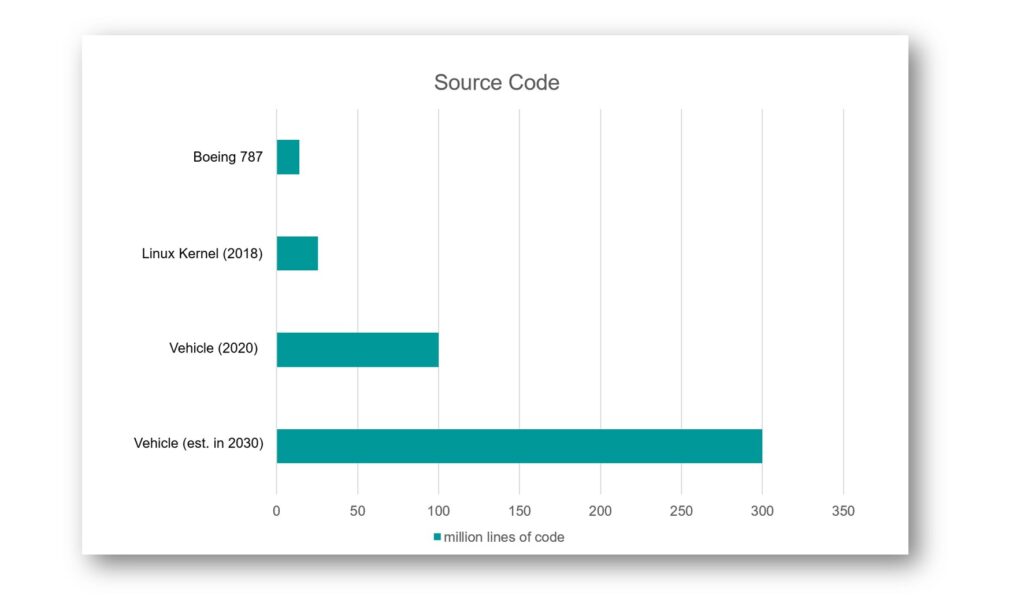
It is expected, that automotive becomes (if not already) the largest software supplier, which comes with significant cybersecurity risks: hackers try to seek access to the system and by that threaten safety functions or consumer privacy. In 2018, UN ECE’s WP29 began addressing binding requirements for car manufacturers (and as consequence also Tier 1 and Tier 2 suppliers). This resulted in the before mentioned release of
- UN Regulation No. 155 – Cyber Security and cyber security management system
- UN Regulation No. 156 – Software update and Software update management system
While the latter provides a framework for necessary processes around delivering software updates towards target system, we take a closer look towards UN R155, CSMS (formerly known as WP29/Trans/79).
Start acting now
UN R155 is binding for new vehicles in the UNECE markets by July 2022. Japan indicated to apply this already in January 2022. For legacy vehicles the regulation is going to be applicable by 2024. This puts enormous pressure on OEMs and their supply chain, since a certification is required to release cars in the markets being part of UNECE. In addition, showing the capability to manage cyber security aspects provides mutual trust towards customers.
The UN R155 regulation is split into 2 main requirements towards the OEMs when aiming for type approval: 1. OEMs have to implement a Cyber Security Management System (CSMS). 2. Show that with the CSMS the OEMs implement an auditable evidence of decisions around security aspects. The regulation even provides examples for threats, their mitigations and security control item. In other words, the regulation clearly shows what is to be done. But it doesn’t provide guidance of the how. And it doesn’t include Tier 1/2 suppliers.
Introducing ISO/SAE 21434
ISO/SAE 21434 is currently available in final draft, expected to be released in August 2021. The currently available version cannot deny its relationship to ISO 26262. Due to the nature of modern technology aspects (already outdated when released), ISO/SAE 21434 focuses on providing guidance for good techniques on addressing cyber security relevant validation. Several clauses inside the standard deliver answers on implementing a good cyber security culture, what to do when throughout the product lifecycle and how to manage the supply chain concerning cyber security. Focus lies on methods around risk analysis (clause 8) and the concept phase of a development (clause 9).
Use the pre-configured objects to quick-start your threat and risk analysis. Refine and adjust to your process if needed easily.
Use the standard revision security and baselining function to restore historical states for audits at any time.
Use linking capabilities to connect the cyber security analysis objects with your existing development process.
Polarion is predestined to support OEMs and Tier 1/2 in implementing the requirements arising from both UN R155 and ISO/SAE 21434 already with several of the build in functionalities. Together with the additionally available ISO/SAE 21434 project template, organizations receive a perfect support to manage all requirements around the UN R155 and ISO/SAE 21434.
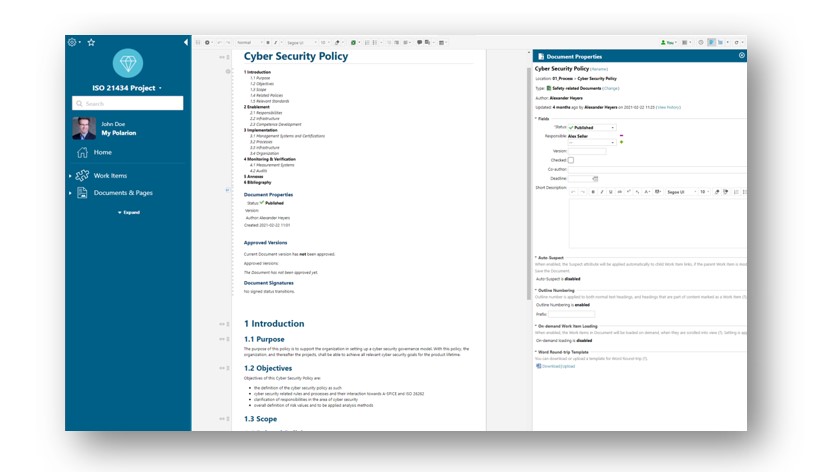
The template consists of document templates, which help organizations to document their cyber security readiness together with the managed assets in one place. Not only provide the documents a predefined workflow with a permission model and baselining options, they can also be re-used across projects for saving time and gaining quality.
Clause 9 of the standard requires to analyze whether an Item is cyber security relevant. Typically, the Items are representations of a component or system – they do not stand alone. Our ISO/SAE 21434 template anticipates different development processes by linking the cyber security object Item to a system representation, as shown in the picture below. It is irrelevant whether the component is in another project and which development process it is based on. Use the picture as example.
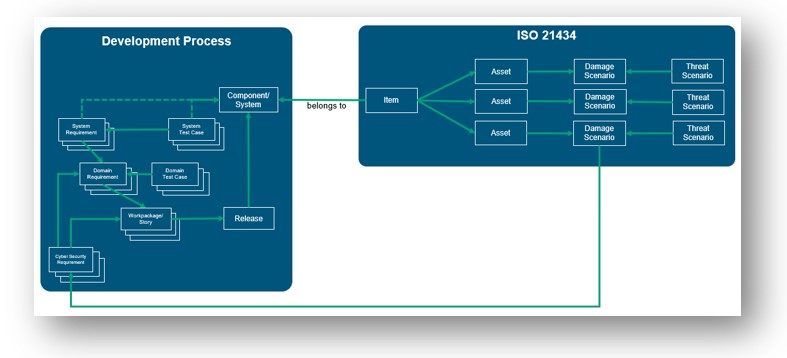
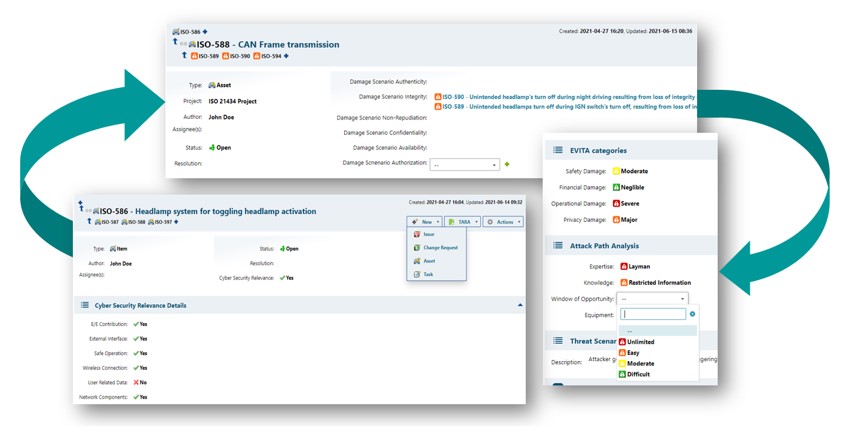
The key aspect of both UN regulation and standard is to deliver secure products. A continual TARA (threat and risk analysis) shall be performed throughout the lifecycle. The Polarion project template helps users by providing the required objects such as Assets, Damage Scenario or Threat Scenario. Each object has the necessary attribute information and a customized life cycle. This helps users to start the analysis immediately according to ISO/SAE 21434. The underlying risk classes are based on Microsoft’s STRIDE, which can be used for the analysis of the assets. Damage and Threat Scenario scores follow the definition according to the EVITA project, which was also referenced in SAE J3061. Altogether, this ultimately leads to the final risk class. In addition to the shown attack-based method, CVSS2 or attack vector-based approaches can also be implemented.
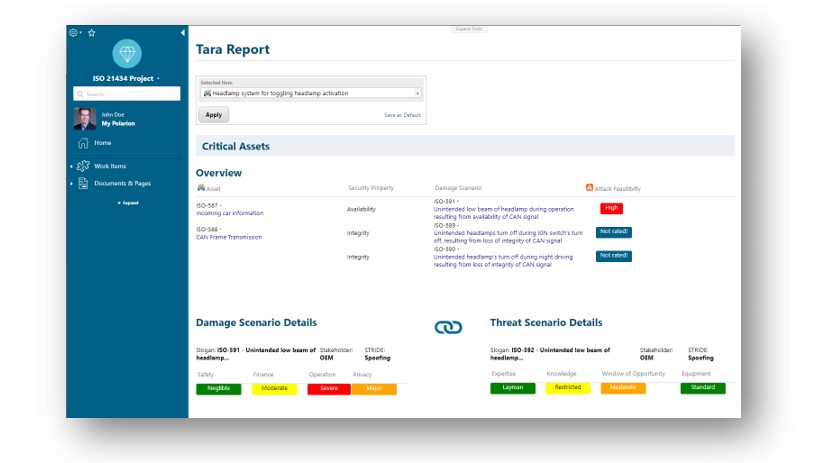
Customized reports provide an immediate status report to identify the threat scenarios for individual items and derive activities accordingly. Through the standard revision security and baselining function, historical states can be restored and proven for audits at any time.
Due to the provisional nature of the standard, it remains to be seen how the approval authorities will conduct audits and interpret the requirements, especially towards Tier 1 and 2 suppliers. The Polarion template is based on the current state of knowledge. Due to the flexibility of Polarion to adapt the project templates, users are able to address changes at any time. Later this year, we will also integrate another add-on for static and dynamic code analysis against threat scenarios and consider the new ISO PAS 5112 for auditing.
Contact us
Want to learn more? Do not hesitate to get in touch with us via the contact page.
References
[1] UNECE Press Release, UN Regulations on Cybersecurity and Software Updates to pave the way for mass roll out of connected vehicles, https://unece.org/sustainable-development/press/un-regulations-cybersecurity-and-software-updates-pave-way-mass-roll, June 2020
[2] Upstream Security Global Automotive Cybersecurity Report 2019, https://upstream.auto/upstream-security-global-automotive-cybersecurity-report-2019/
[3] GSA with McKinsey, Cybersecurity in automotive, https://www.mckinsey.com/~/media/mckinsey/industries/automotive%20and%20assembly/our%20insights/cybersecurity%20in%20automotive%20mastering%20the%20challenge/cybersecurity-in-automotive-mastering-the-challenge.pdf, March 2020
[4] ISO/SAE DIS 21434 Road vehicles – Cybersecurity engineering https://www.iso.org/standard/70918.html
[5] EVITA – E-safety vehicle intrusion protected applications, https://www.evita-project.org/ [6] Microsoft Threat Modeling Tool threats, https://docs.microsoft.com/en-us/azure/security/develop/threat-modeling-tool-threats