The importance of a CAD security strategy

Never in the history of humanity has the globe been as connected as it is in 2023. Globalization means that individuals are free (to a degree) to go wherever they want, whenever they want. From a business perspective, companies operating internationally can tap into new supply chains, access more data and recruit an incredibly diverse and talented work base, taking their competitive advantages to the next level.
There’s an elephant in the room, one that will never truly be eradicated: the importance of a CAD security strategy. A company’s CAD security strategy can be defined as the resources and processes required to ensure a company’s Intellectual Property, upcoming product releases and engineering data remains protected. Additionally, a solid CAD security strategy will protect against cyber attacks, thus limiting the chances of CAD data becoming compromised.
Whilst companies rightly continue to invest substantial resources into R&D and innovation to stay ahead of the competition, there needs to be a clear security strategy; without one, all of the incredible work done by companies to innovate and stay ahead of the competition will ultimately be for nothing.
The following blog will focus on the importance of a CAD security strategy, and how Siemens continues to provide solutions that are as secure as possible.
All information throughout this blog is underpinned by a CAD security study conducted by Lifecycle Insights. To read the full study, click the link below and download the FREE eBook 👇
Why is data protection so important?
A successful CAD security strategy consists of many different elements and moving parts. For this particular blog, we want to pay close attention to data protection. How can data protection be defined?
DATA PROTECTION : A DEFINITION
The relationship between the collection and storage of key, sensitive data. Data protection processes can be governed by external factors, such as government directives, but are typically determined by the individual company.
Sure, any company can implement a security strategy to some capacity, but how can companies differentiate the strategy? What is the significance of adapting an aggressive strategy vs implementing the bare minimum?
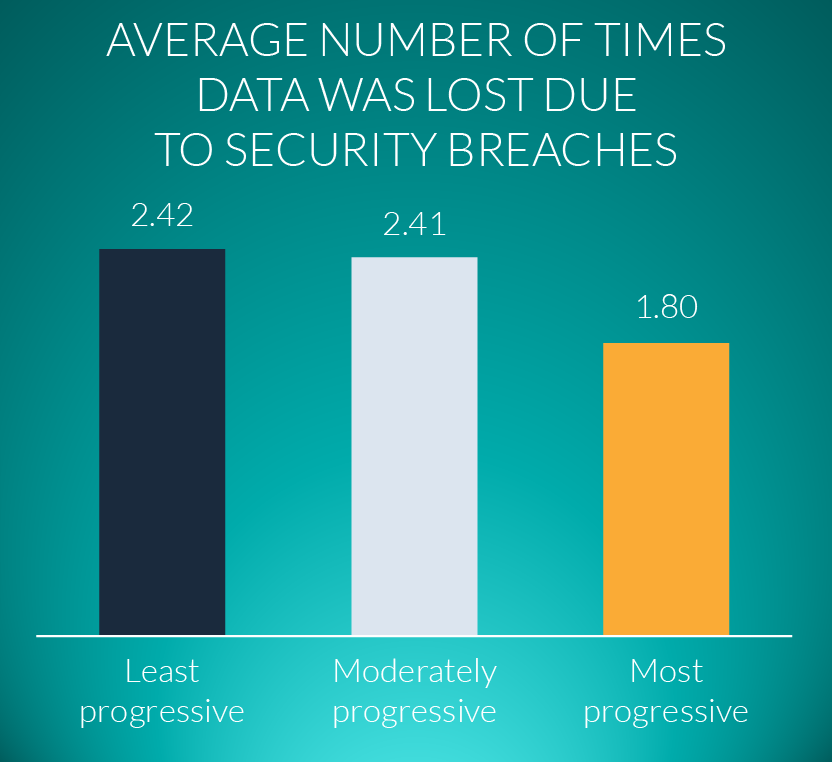
The study conducted by Lifecycle Insights indicated that there are negligible gains between the least progressive and a moderately progressive security strategy in terms of data lost due to a security breach: companies adapting either level of security lost data to security breaches approximately 2.5 times a year.
Serious gains are attained however for those companies adapting an aggressive security strategy. Companies with an aggressive strategy only lose data to security breaches, on average, 1.8 times a year – a substantial decrease of 26%.
This is important. Sure, more resources may be needed upfront to implement an aggressive CAD security strategy, but the benefits generated more than make up for the resources required. It’s not just a reduction in data breaches, but companies can have greater confidence in their systems, thus resulting in more resources diverted to innovation and R&D to stay ahead of the game. This symbiotic approach to security and innovation leads to a greater competitive advantage, and should be an approach all companies seek to take.
A case study
Let’s take a look at a leading Silicon Valley cell phone manufacturer, who continuously adopt an aggressive security strategy across their diverse portfolio of products. Multiple security updates are rolled out on a regular basis to ensure users are protected against the latest threats. Additionally, users continue to use their products with confidence; whether this is through hardware security or biometrics, encryption and data protection features, or operating within a safe application. It is clear there are a plethora of security features available.
It isn’t just the security features available to consumers; the reason the strategy is so effective is the user experience and manageability of such features, combined with a seamless integration between hardware and software. Cell phone manufacturers have moved, or are in the process of moving, toward facial and bio-metric identification as a security feature, whilst consumers also maintain complete control over identification, password management and payment methods. Companies can have the strongest data protection strategy, but it can be rendered futile if the user experience and manageability isn’t efficient.
Our approach at Siemens
The aim for companies is simple: to create the securest system that they possibly can within the market, and Siemens is no different. Siemens continues to adopt industry-leading cyber security strategies. Our holistic approach makes it possible for you to introduce and maintain a digitized organization securely and responsibly.
We always work to re-enforce our protection across all products and services, and that includes NX™ software too. A continuous release cycle, where we introduce a new release to the market every 6 months, ensures you have access to the latest and greatest features on the market, whilst simultaneously having the best protection available against external threats. This holistic, continuous release approach to security aims to build trust and confidence in the user-base.

There will always be security risks
As we’ve mentioned before, the goal at Siemens with our holistic approach to cyber security is to build trust, and to ensure you are completely protected. That’s the goal, but we know that it is difficult, almost impossible to create a 100% secure environment. An inter-connected world means externalities that are hard to predict and control will always be seen as a threat to cyber-security. Additionally, individuals and organizations who exploit companies through security threats continue to be smart, nimble and look for new ways in which to compromise data protection and security. Companies are only as secure as the IT environments that they operate in, and are fully aware of the evolving threats they are up against. And this can be backed up by International Data Corporation (IDC) research that predicts global security spend will reach $219bn in 2023, and is expected to increase to $300bn in 2026.
Conclusion
And that draws this CAD security blog to a close. It is absolutely imperative that companies aim to bolster their CAD security strategies, and ensure their data remains as secure as possible. As security strategies and features continue to become more effective, so does one’s ability to find their way into a company’s ecosystem. Strategies need to integrate hardware and software security simultaneously and require significant upfront collateral. This enables companies to adopt the most aggressive security strategy possible, increasing their defense against data protection incidents as a result.
To find out more, take a look at the full Lifecycle Insights study below.
Continue your journey with CAD security
Read the full CAD security study | A Lifecycle Insights & Siemens collaboration

Lifecycle Insights CAD security study
Lifecycle Insights conducted a bespoke study. The results of this survey-based research project reveal the issues companies face related to CAD security, and the strategies they are adopting to manage those risks. This eBook shares the study findings, as well as recommendations for developing an effective plan to combat common CAD security failures. Take a look by clicking the button below 👇