Selective hardening in space applications

Introduction
The space sector continues to experience disruption as innovation drives the creation of new business models across government and commercial entities. Low Earth Orbit (LEO) constellations, Traffic and Management applications, and advanced communication systems are just a few examples where innovation is driving the next generation of semiconductor development targeted for space based applications.
With 2000+ space technology startups competing with the traditional players, it’s easy to conclude that the race is on. Semiconductor vendors face continuous pressure to reduce program cost, schedule, and increase the frequency of spins. These demands are accompanied by (and in conflict with) the need for the next generation of performance, advanced features, and tightening power budgets.
Thrown into the mix here is how project teams design and verify their ICs effectively mitigate against single event upsets. Two sub-themes are emerging to meet market demands. The first theme is a renewed interest in leveraging commercial high-reliability libraries to accelerate the development lifecycle. The second them is a growing desire to reduce cost through selective hardening by only protecting circuits critical to mission functionality.
Selective Hardening Challenges
Feedback from industry suggests that the traditional approach to SEU mitigation has many pitfalls and leaves two important questions unanswered.
- For the design elements known to be mission critical, how effective is the implemented mitigation?
- How can I identify the potential of failure due to faults in design elements not protected?
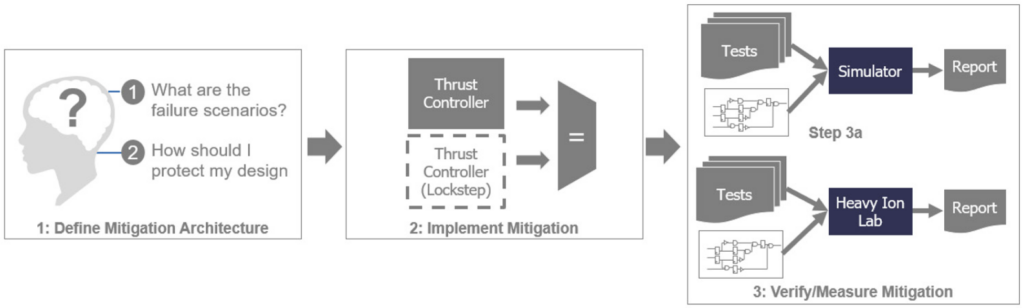
The traditional approach to SEU mitigation is best summarized in a three-step workflow.
- Step 1: Identify failure points through expert driven analysis
- Step 2: Design engineers insert the mitigation (HW and/or SW)
- Step 3: Verify the effectiveness of the mitigation
- Simulation leveraging functional regressions and force commands to inject SEUs
- Post-silicon functional testing under heavy ion exposure
Unfortunately, the traditional approach has multiple drawbacks, including:
- No common measurement (metric) which determines the effectiveness of SEE mitigation.
- Expert driven analysis is not repeatable or scalable as complexity rises.
- Manually forcing faults in functional simulation requires substantial engineering effort.
- Inability to analyze the complete fault state space using functional simulation and force statements.
- Late cycle identification of failures in beam alongside limited debug visibility when they occur.
Methodology and Workflow
Working with partners, Siemens has developed a methodology and integrated workflow to deliver a systematic approach in measuring the effectiveness of existing mitigation as well as determining the criticality of unprotected logic.
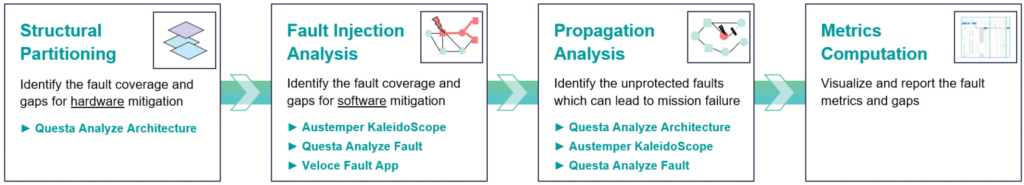
Structural Partitioning: The first step in the flow leverages structural analysis engines to evaluate design functions in combination with hardware mitigation implemented to protect the function.
Fault Injection Analysis: Mitigation which could not be verified structurally are candidates for fault injection. In this phase, SEUs are injected, propagated, and impact evaluated.
Propagation Analysis: The SEU sites left unprotected are evaluated structurally and under expected workload stimulus to determine per site criticality and their ability to result in functional failure.
Metrics Computation: Data from structural, injection, and propagation analysis feed the metrics computation engine and visualization cockpit. The cockpit provides insights into failure rate, the effectiveness of the mitigation, and the gaps which exists.
Every semiconductor development program has unique characteristics. The methodology described above is flexible and highly configurable, allowing project teams to adjust as needed.
Conclusion
Mitigation of single event upsets continue to challenge even the most veteran project teams and this challenge is exacerbated as design complexity rises and technology nodes shrink. New methodologies exist to provide quantitative results detailing the effectiveness of SEE mitigation.
For a more detailed view of the methodology, please refer to the white paper which can be accessed on Verification Academy or Siemens.com :


