Trading off security for cloud benefits

The State of the Cloud Transition
Why are some manufacturers still uneasy about adopting cloud software for product innovation and engineering? The benefits are clear, as we discussed in our prior posts, The Subtle Shift to “Why not Cloud?” and Cloud Engineering Software: More than Engineering Software on the Cloud. But the transition started out slowly.

For a while, one of the most significant inhibitors to cloud adoption was a lack of “apples to apples” capabilities between traditional applications and those available on the cloud. But that disparity is no longer the issue as we discussed in our Why Not to Justify Buying Cloud Engineering Software post. So what’s leaving manufacturers hesitant about cloud migration?
For some companies we speak to, security still makes them uncomfortable starting their cloud transformation. It’s an important issue and one that they must consider. Let’s take a look at how companies perceive the security-cloud benefits trade-off, the reality of the situation, and what they can do to objectively evaluate risks and rewards.
Security is a Scary Topic
Security is a challenging topic. No company wants to put their critical product data at risk. Stories about intellectual property theft and hacking are common occurrences, and manufacturers are rightly concerned. The threat is real whether company data resides inside their firewall or with a web services provider. There is always risk, regardless of the deployment approach. But risk is something that can be managed by taking a thoughtful approach to it.
Evaluating the Security – Cloud Benefits Tradeoff
Companies need to know how to make a logical tradeoff between the value of the cloud and the increased risk it brings. But is that the question to be asking? Is the risk higher on the cloud? It depends on many factors, but in most cases, it’s not the appropriate question.
It’s true that the cloud is a more attractive target, particularly when data consolidated from multiple companies. Similar to a bank, it’s a more attractive target because there is typically more to steal from one location. But, like a bank, it’s likely to have better protection than one person or company could provide on their own. Web services companies can afford dedicated resources that many companies could never attract, afford, and retain. They also have specialists to cover different security disciplines, for example, encryption or intrusion detection. In addition, web service providers give companies someone to turn to in the unfortunate event something does happen. Many companies we speak to consider security to be a positive feature of the cloud as opposed to an issue.
Managing Risk
Whether or not the risk is greater or not, the cloud changes the risk profile and must be managed. Fortunately, the IT community has gained significant experience in procuring and operating cloud solutions. Companies today can leverage best practices developed from experience.
Some best practices are general, while others are more specific to product IP. One common approach to protect design data is to store only partial data in one place. It’s not uncommon for companies to keep some very special trade secrets in a separate location, or undocumented. For example, they may choose to share the 3D specifications for a part but not share the manufacturing techniques required to achieve the desired quality. Or, they may choose to store tolerances at lower precision.
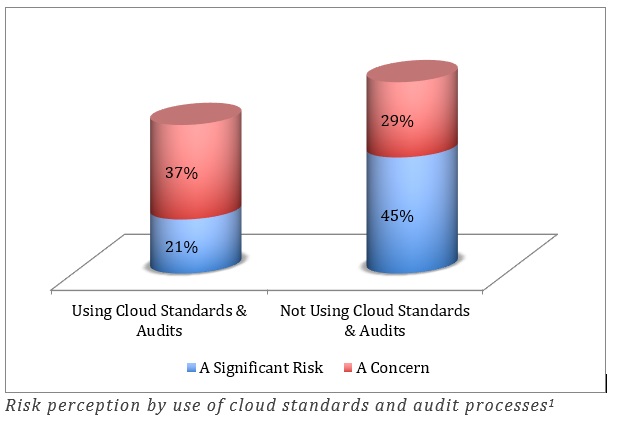
Other security best practices work across multiple types of solutions. These include practices like using industry standards and audit procedures. In some cases, customers or industries mandate specific techniques. Our research shows that although companies are concerned about the risk, those companies that have implemented standards and audits see the security risk as less critical than those that haven’t implemented them (figure). These companies don’t face lower risk, necessarily, but they have chosen to mitigate the risk proactively.
The Bottom Line on the Security – Cloud Benefits Tradeoff
Companies are beginning to realize that their critical product data is probably just as safe, if not safer, on the cloud due to the enhanced security measures afforded by shared resources. But security is an important issue, and companies should evaluate it carefully. To be more comfortable making the cloud transition and take advantage of the available benefits, manufacturers should:
- Educate themselves on the reality of the security-cloud benefits tradeoff
- Include standards in the supplier evaluation process
- Ensure that the partner allows security audits
- Follow best practice standards and audit processes
In the end, the important things are to work with a trusted supplier and be smart about it. What does this look like from your perspective?
1Source: Additional analysis of data from Adopting Cloud Innovation Platforms survey of over 200 manufacturers
About the author:
Jim Brown is the founder and President of independent research firm Tech-Clarity. Jim is a recognized expert in enterprise software for manufacturers, with over 25 years of experience in application software, management consulting, and research. He has extensive knowledge about how manufacturers use Product Lifecycle Management (PLM) and other enterprise applications to improve business performance.
Jim is actively researching the value available from new initiatives and technologies including cloud computing, digitalization, product innovation platforms, smart manufacturing, AR, VR, and the IoT in addition to his core research areas which include PLM, quality, service, manufacturing, and more.


