Embrace Digital Rights Management

Control Access and Usage of Product Data Across the Enterprise
No organization is safe from data security risks today. This contributes to the rising demand for advanced Digital Rights Management solutions. In a product development world, collaboration is paramount for business success, where controlling and managing intellectual property (IP), data security has become a major challenge for businesses. Every day, data security is becoming more and more important and vital to business operations and success. Unfortunately, intellectual property theft is on the rise. A survey of leading executives indicates that mishandling product data by insiders, suppliers, and partners is the leading cause of intellectual property breaches.
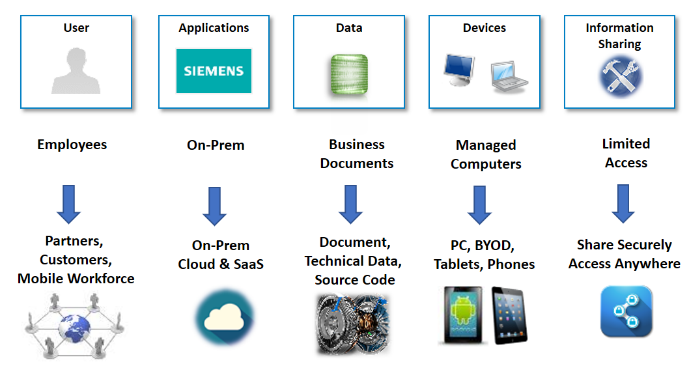
Let’s look at the need for digital rights management and the changing landscape of security caused by shifting business requirements. Today, companies need to share information not just with internal employees, but also with partners, customers, and even partner’s partners. Similarly, IP data is no longer just business data which is usually stored in the office/pdf file format, but now includes technical data such as CAD/images/source code and so on. BYOD (Bring your own device) consumerization and mobile have pushed corporate IT to support not just managed computers (provided by company), but also non-company owned devices. Cloud apps drive a lot of data stored outside of the traditional on-prem applications, Security Landscapehence the need to protect data both on-prem and on the cloud. At the same time, the need for businesses to share data and collaborate has greatly increased in order for them to stay competitive. Companies cannot just store and protect their IP data in a closed room or network and have a very manual restricted process to access data. They need to protect their IP data, while still enabling, sharing, and allowing authorized users to access data, anywhere.
Under this situation, protecting sensitive intellectual property from data leakage or theft, controlling the access and usage when shared with employees, partners, and suppliers, and complying with applicable regulatory requirements has become a critical need for business success.
To better understand the security challenges and associated risks to business success, we have to look at some of the key business scenarios where digital rights management comes into play.

To begin with, let’s look at the global engineering collaboration scenario, where data needs to be shared across divisions and geographies (say in a multisite environment). This scenario poses challenges of controlling data access for need-to-know projects, new product introduction (NPI) and to meet global regulatory export requirements. This brings the risks of violation of global regulatory export requirements and the possibility of misuse of NPI engineering data shared outside team members.
Similarly, supplier collaboration has become an integral part of businesses today, where product data needs to be shared with suppliers so that they can design, manufacture and test components. Suppliers may need to modify information to fit into their processes and also share data with their partners and/or suppliers. Under this situation, loss or theft of IP is common, while timely and accurate access to the correct product data is critical to control costs and project timelines.

At the same time, partner collaboration has become common where multiple companies (sometimes competitors) collaborate to develop and manufacture new products. Both companies must share and jointly develop intellectual property (IP) while protecting the IP of their partners. Lack of adequate controls to enforce protection of IP put contractual obligation at risk for all parties.
Today, after-market service business has become critical for many manufacturing companies and the risk of IP theft by insiders and competitors is a direct threat to the service revenue. Field service representatives need access to technical data (in different formats), product manuals and service instructions on their laptops and mobile devices to accomplish their job effectively on the field. This scenario poses the challenge of securely sharing technical data to a remote or mobile workforce and poses the risk of company IP and customer confidential data loss due to lost or stolen devices, along with insider threats of remote employees stealing know-how and service customers.
Simultaneously, regulatory compliance needs such as ITAR, EAR, GDPR, DFARS, and HIPPA are becoming more and more stringent. These compliance needs can impose significant penalties for non-compliance (example in case of GDPR, the cost is up to 4 percent of annual global revenue or €20 million, whichever is greater), reputational damage, and individual private claims. As a result, it has become important for organizations to fully comply with these regulations, by enforcing and demonstrating the high standard of data protection and IT security, while also achieving global collaboration.
To address the above data security challenges and associated risks, organizations are spending considerable time and costs in traditional security approaches. Traditional approaches include protecting data by guarding networks and endpoints, Source: Federal Data Protection Report: 2018 which unfortunately ends at the network perimeter. This also calls for cumbersome management for each disparate system and data set. These approaches also heavily rely on manually intensive static processes, are prone to human errors.
Today, more and more organizations are realizing that the previously mentioned traditional approaches to security are no longer sufficient to protect the IP of the company with the changing security landscape.
Organizations are looking for enterprise-level digital rights management (DRM) solutions that can work with any application, document or file, and protect data wherever it goes. It should be able to monitor critical data usage in real-time. The DRM solution should be dynamic in nature, enabling real-time decisions based on the most up to date factors. It should be transparent to end-users without impacting productivity. All this at a lower total cost of ownership.
Why Embrace Teamcenter Digital Rights Management?

We introduced Teamcenter Digital Rights Management (Teamcenter DRM) to help you address these enterprise-level security challenges.
Teamcenter DRM can help you protect your intellectual property (IP) data throughout its lifecycle (at rest, in motion, in use), inside as well as outside of your company.
Teamcenter DRM enables you to securely share, collaborate, and openly exchange high volumes of product data in a complex technical PLM environment across the extended enterprise by:
- Controlling access to data based on data classification, user project assignments, location, and by preventing skirting of access controls when shared via unauthorized channels (for example, email, file server, flash drive), and ensuring data is always up-to-date.
- Enabling complete visibility and control over product data shared with suppliers and also when they share with their partners and suppliers.
- Securely making technical data (including drawings, 3D models and services databases) and service instructions available to a remote or mobile workforce.
- Supporting compliance with industry and regulatory requirements such as ITAR, EAR, GDPR, DFARS, HIPPA and so on.

Teamcenter DRM is an integrated solution that is used to automatically encrypt data files before they can be shared with employees, suppliers, and partners. The encrypted wrapper includes security labels from Teamcenter software that are used to determine the rights of users to access the data. Authorized users can open, view and even modify the protected data files using Rich Client as well as Active Workspace Client and also in native applications, including NX™ software, JT2Go, and Solid Edge® software, where data owners get full visibility into how their data is being shared, accessed and used.
Teamcenter DRM is seamless

We have integrated NextLabs DRM solution natively within Teamcenter to ensure that data stored or extracted out of Teamcenter is consistently protected. It leverages metadata, such as business object IP classifications, projects, user and organization information in Teamcenter to apply rights to files through integration. This means that you do not need to architect entirely new processes or tools to apply rights protection to files. Rather, it happens automatically and seamlessly within a standard user workflow and provides a seamless user experience.
Let’s look at key characteristics of Teamcenter DRM which helps you to address security challenges and eliminate the associated risks effectively at lower TCO.
It protects in real-time by enforcing data access policies to determine whether access should be granted upon request. It allows you to control access and usage on files, such as limiting access, printing, copying, or screen capture, and enforcing time-based rights. It is easy to use and accessible via rich clients, mobile apps, or web browsers and enables you to scale it globally.
It protects automatically and seamlessly with the flexibility to automate the application of rights protection, includ¬ing encrypting and tagging files managed in Teamcenter based on a business context and process. In addition, it allows trusted users in Teamcenter to manually apply rights to files. Metadata such as attributes of a file or document in Teamcenter, or classification can also be used to facilitate the automated process and these attributes can also be embodied within the protected file to facilitate the rights management controls.
It’s device-independent, the protection of the rights on files is persistent and enables external collaboration use cases through mobile devices, tablets, laptops or desktops or uploading to the cloud. The Teamcenter DRM solution enables and embodies this with a zero-client install (Active Workspace) available to enable secure global collaboration.

It alerts you in real-time by storing all the policy decisions and conditions in a central audit server. It provides you visibility into user’s activity through various dashboards and reports in near real-time. You can define your own rules to highlight suspicious behavior and issue an alert. This logging information can be exported into SIEM and other threat detection systems for further analysis.
Teamcenter DRM
- Protects your product or engineering IP from inside and outside threats, while enabling collaboration with suppliers, partners, contractors, manufacturers, and foreign nationals
- Enables a single centralized data security model based on Teamcenter for internal and external access
- Protects IP after it has been accessed/downloaded from Teamcenter
- Protects NX, JT, and other engineering file data types
- Supports offline access for field-service use cases
- Supports sharing (read-only) and collaboration (edit) use cases
- Enables you to terminate data access automatically based on agreed time limits
- Helps you to achieve compliance with global industry and regulatory requirements
- Supports auditing and reporting on data access and usage
Teamcenter Digital Rights Management is the best way to secure your business whilst enabling global collaboration.


