CRA Compliance Made Simple: How Polarion Helps You Stay Ahead

Understanding the Cyber Resilience Act (CRA)
The Cyber Resilience Act (CRA) is a landmark EU regulation designed to strengthen the cybersecurity of products with digital elements—ranging from consumer IoT devices to industrial software. It was signed into law in October 2024 and entered into force in December 2024, with most obligations applying from December 2027. The CRA introduces mandatory cybersecurity requirements for manufacturers, importers, and distributors, ensuring security is embedded throughout the entire product lifecycle—from design and development to maintenance and decommissioning
The CRA addresses two major challenges:
- Low cybersecurity standards in many digital products.
- Lack of timely security updates, which leaves users exposed to vulnerabilities.
By enforcing these requirements, the CRA aims to reduce cyber risks, protect consumer data, and create a harmonized EU-wide approach to cybersecurity compliance
Vulnerability Management Under the CRA
One of the core pillars of the CRA is proactive vulnerability management. Manufacturers must:
- Ensure products are free from known exploitable vulnerabilities before market release.
- Provide security updates without delay and maintain them for at least five years or the expected product lifetime.
- Report actively exploited vulnerabilities within 24 hours to national CSIRTs, followed by detailed reports within 72 hours and mitigation details within 14 days.
- Establish coordinated vulnerability disclosure policies, including clear reporting channels for third parties and security researchers3.
These measures shift responsibility from end-users to manufacturers, making cybersecurity a precondition for market access. Non-compliance can result in fines of up to €15 million or 2.5% of annual turnover
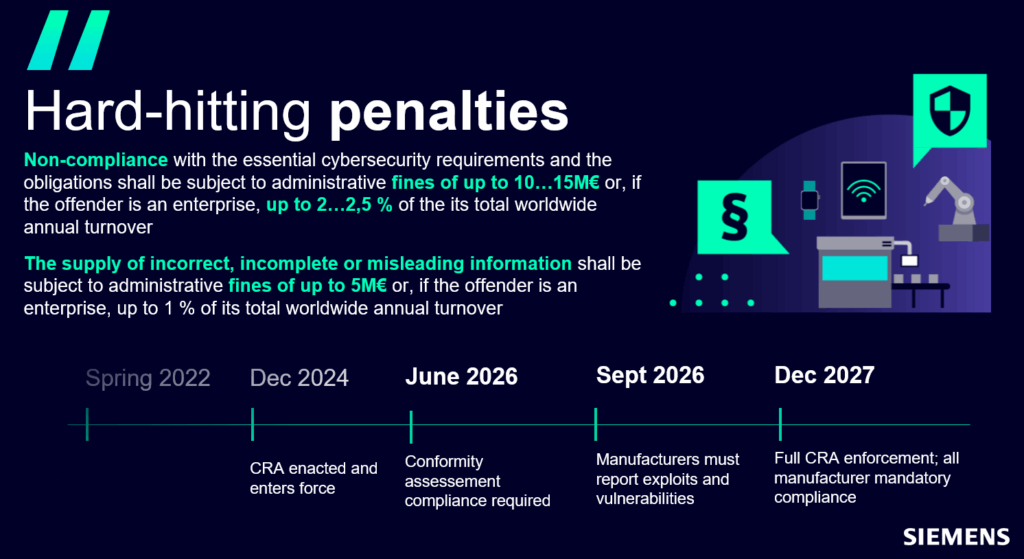
The Role of SBOM in CRA Compliance
The CRA also mandates the use of a Software Bill of Materials (SBOM) as part of technical documentation. An SBOM provides a transparent inventory of software components, helping identify and manage vulnerabilities in third-party and open-source dependencies. Key points include:
- SBOMs must cover at least top-level dependencies.
- They must be machine-readable and follow recognized standards like SPDX or CycloneDX.
- SBOMs are not required to be public, but must be available to market surveillance authorities upon request
By requiring SBOMs, the CRA promotes supply chain transparency and enables faster vulnerability remediation.
How Polarion Supports CRA Compliance
Secure Product Lifecycle
A Secure Product Lifecycle comprises three essential phases:
- Concept: Begin with cybersecurity risk assessments to proactively identify potential vulnerabilities. Establish clear security requirements that will steer the entire development journey.
- Development: Employ secure coding practices and conduct frequent security testing. This ensures vulnerabilities are effectively addressed before the product reaches the market.
- Operation: Maintain cybersecurity resilience by continuously monitoring for new vulnerabilities. Apply patches without delay and perform regular security audits to safeguard the product.
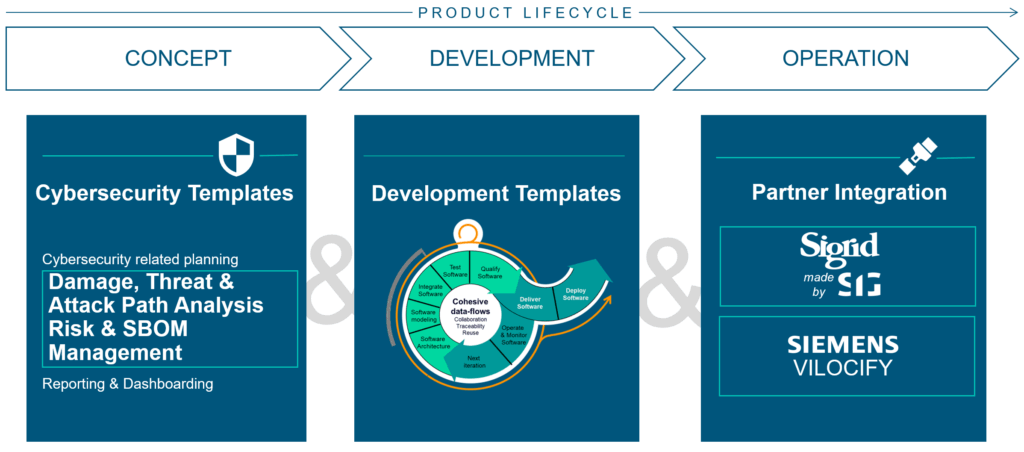
Polarion provides comprehensive solutions tailored for each phase of the product lifecycle. We’ll explore these in greater detail later in the blog post.
Concept Phase: Threat and Risk Analysis
Starting with the Threat and Risk Analysis (TARA) as part of the Concept phase, our solution, available since 2023 as part of the Polarion X Automotive Package, offers a comprehensive data model for managing TARA. It includes workflows, link relations, and interactive reports. We equip users with tools to define items under analysis, perform impact ratings for damages, and calculate the feasibility of threats. Furthermore, our solution facilitates the management of damage and threat scenario libraries, leading to the identification of risks and their mitigation actions. These mitigation actions can subsequently translate into new requirements for the product, ensuring its continued resilience and security.

Development Phase: Flexible Development Methods Combined with SBOM Management
In the Development phase, Polarion offers unparalleled flexibility by supporting a variety of development methodologies, including the classical V-model and agile frameworks. This allows teams to adopt methods that best suit their projects and products, as already detailed in various other blog entries. Building on this robust foundation, we are excited to introduce our latest feature: Software Bill of Materials (SBOM) handling. This new capability empowers development teams to efficiently document and manage the components and dependencies within their software, enhancing transparency, traceability, and security throughout the development process.
Our SBOM management solution integrates seamlessly with Jenkins as an existing build solution. We have further enhanced it to support more generic build pipelines, allowing for the extraction of SBOM information directly from the pipeline process. The generated data is stored comprehensively in a centralized library, which manages all SBOM components in one place. This centralized approach enables decision-makers to effectively oversee critical components, addressing potential license or security issues during the development phase itself.
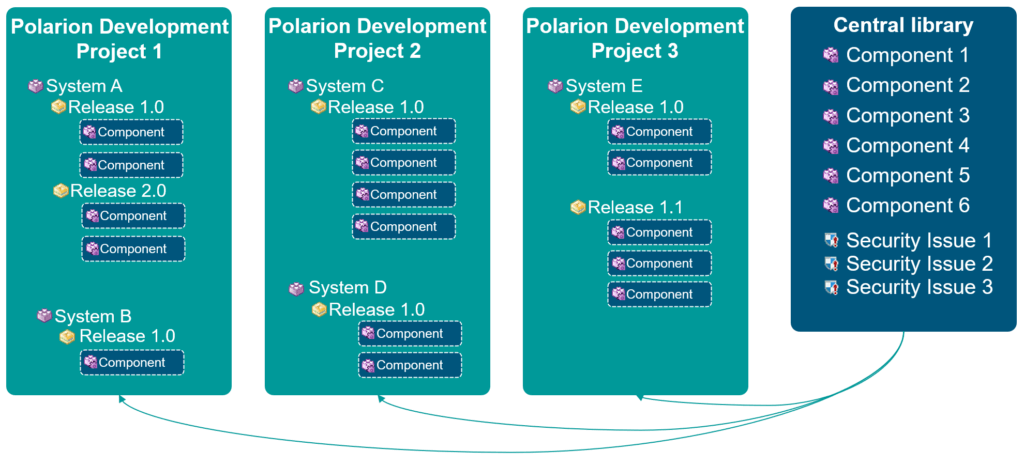
In addition, the central library includes dashboards that provide an at-a-glance view of component statuses throughout the development phase. These dashboards empower decision-makers by offering real-time insights into potential risks, ensuring that any license or security concerns can be promptly and effectively managed as they arise.
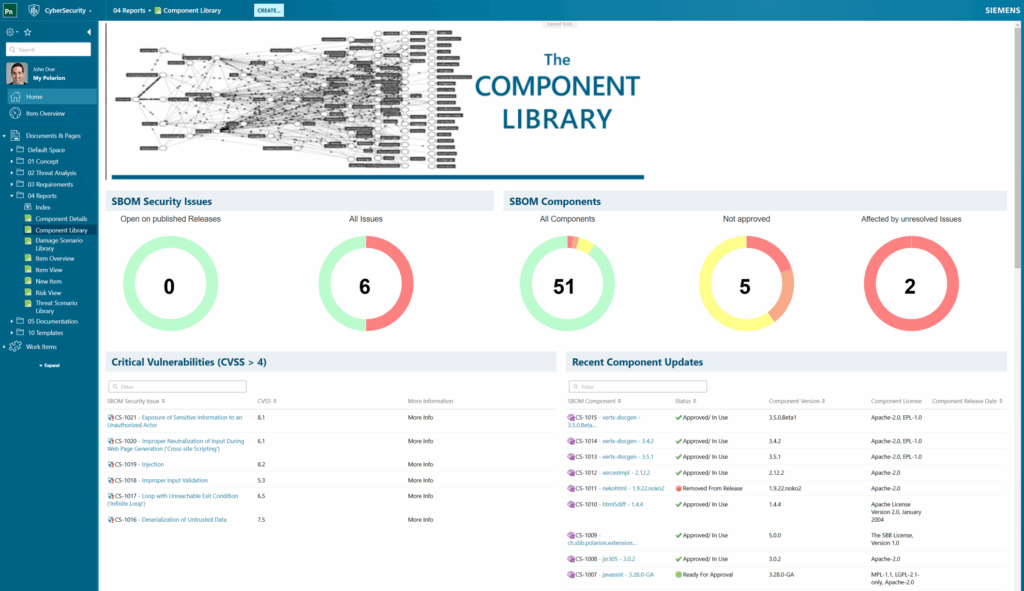
Development Phase: Integrating Sigrid for Enhanced SBOM Management and Proactive Code Quality Improvement
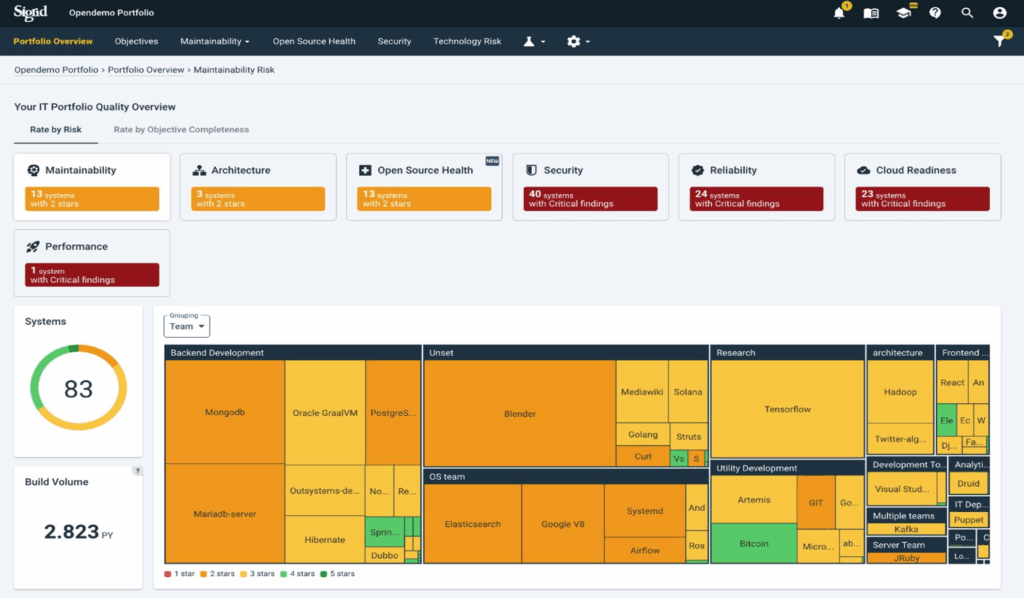
Sigrid is a platform developed by Software Improvement Group (SIG) designed to enhance software quality and performance. It caters to organizations aiming to improve their software systems by providing detailed insights into code quality, maintainability, security, and risk management. With Sigrid, users can conduct automated code analysis across multiple technologies, gaining valuable feedback that helps developers and decision-makers make informed improvements.
We are thrilled to offer an integration between Polarion and Sigrid, enabling our clients to leverage Sigrid’s powerful capabilities seamlessly within their workflows. This integration allows clients to connect Sigrid’s analysis results directly with our processes, enhancing productivity and decision-making. Sigrid serves as an alternative to the previously described build pipeline by not only delivering SBOM components with detailed license and security issue information but also providing early insights into code quality. This proactive approach, often referred to as “shift left,” empowers teams to implement corrective actions during the development phase, ensuring higher quality outcomes and reduced risks.
An alternative to the integration with Sigrid is our integration with Siemens Vilocify. This solution focuses on reporting security issues and providing engineers with advisories to mitigate potential vulnerabilities. Vilocify can be utilized either as an alternative to Sigrid or as a complementary addition, enhancing the robustness of our security management framework.
Operation Phase: Leveraging SBOM and Traceability for Comprehensive Vulnerability Management
The Cybersecurity Resilience Act mandates security updates for a minimum of five years. While typical web applications in a DevOps environment can receive updates “on-the-fly,” the scenario differs significantly for software embedded in physical products that are deployed without direct vendor access. Consequently, it is crucial to maintain a comprehensive understanding of which software components and their specific revisions are deployed in the field. This awareness is essential, particularly as critical vulnerabilities can emerge at any time post-release, necessitating thorough analysis and prompt remedial actions.
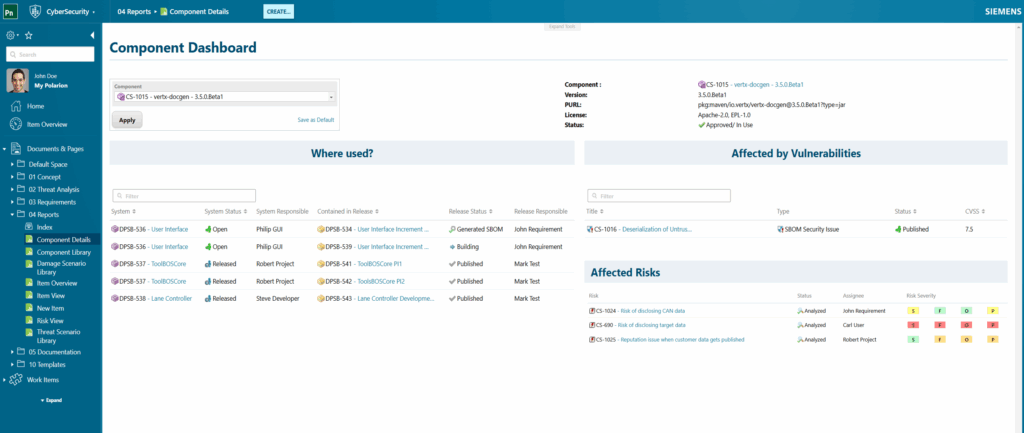
Since Polarion manages the SBOM details, our comprehensive reporting capabilities, such as the “Where Used” analysis, enable precise tracking of which component in which revision is included in specific software releases. This functionality seamlessly connects to the risk analysis conducted during the Concept phase. With Polarion’s unique traceability capabilities, we ensure that all information across different lifecycle phases is interconnected, facilitating a thorough analysis of the real criticality of a given vulnerability within the context of the entire system.
What’s next?
The new template is going to be available with Polarion 2512 as Polarion X and on-premises solution. Interested clients can already apply for an Early-Access-Program. To apply for the EAP, reach out to Thomas Richter